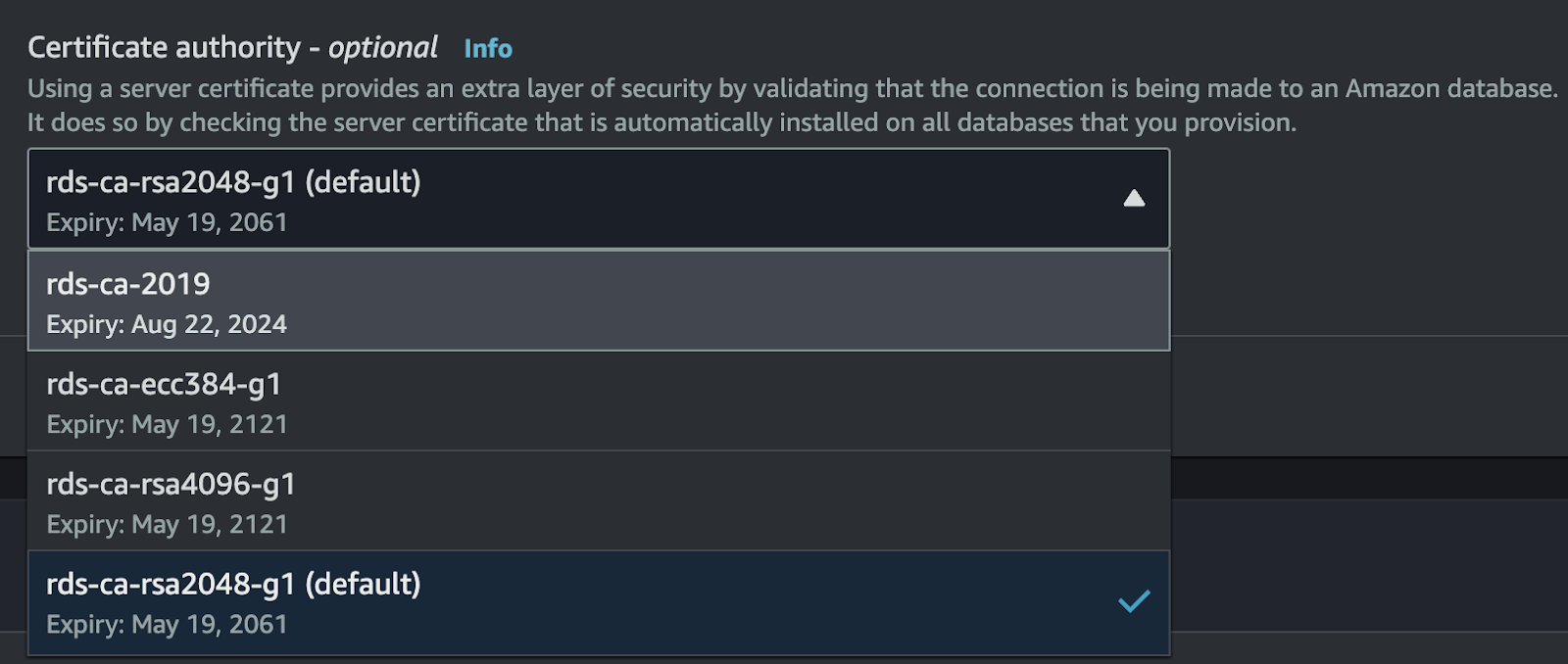
Amazon periodically rotates the Certificate Authority (CA) key that’s used to sign TLS certificates that encrypt connections to Amazon Relational Database Service (RDS) instances. The next certificate expiration is happening in August 2024, so you’ll need to make sure you update the CA certificate that’s being used on your RDS instances.
In the future, you shouldn’t have to worry about rotating your CA certificate configuration as frequently, as expiration dates are much further out. Here’s the list of CA certificates that you can currently select from when provisioning a new Amazon RDS instance running the latest MySQL version. The next earliest expiration date is at least 30 years away, in 2061.
In the AWS Management Console, the Amazon RDS service has a Certificate Update section that shows you which RDS instances require rotation of the CA certificate. However, this user interface feature only targets the current region and AWS account.
Using AWS Config for Compliance Checks
The AWS Config service is specifically designed to help you identify cloud resource configurations that do not comply with your organization’s policies. AWS Config includes a library of built-in “rules” that you can enable for your account. However, you can also build custom rules for AWS Config, using two different approaches:
- Custom Lambda Rules
- Custom Policy Rules (uses Guard syntax)
Developing custom Lambda functions for AWS Config to detect resource compliance requires a higher level of development and testing effort. However, in August 2022, AWS announced support for authoring AWS Config compliance rules using Guard syntax instead. Originally, Guard was designed to be used for validating CloudFormation templates. Guard rules use a limited, Domain-Specific Language (DSL) for writing declarative validation rules.
You can define a custom AWS Config rule that checks your Amazon RDS instances to see if they’re using the expiring certificate or not, using Guard.
Enable AWS Config Recording
Before you can implement a Custom Policy Rule for AWS Config, you’ll need to enable AWS Config “recording” for your AWS accounts. This simply tells the AWS Config service that you want it to periodically scan your cloud resources, in your AWS account, and gather the “current state” configurations for each of them. AWS Config stores this data internally, so you can evaluate each resource for compliance.
- Login to the AWS Management Console
- Navigate to the AWS Config service
- Click the Get Started button
- Choose All Resource Types for Recording Strategy
- Choose Continuous Recording for Recording Frequency
- Click Next, then Next to skip rules, and Confirm
Once you’ve enabled the AWS Config service, it will immediately start tracking changes to resource configurations across supported services.
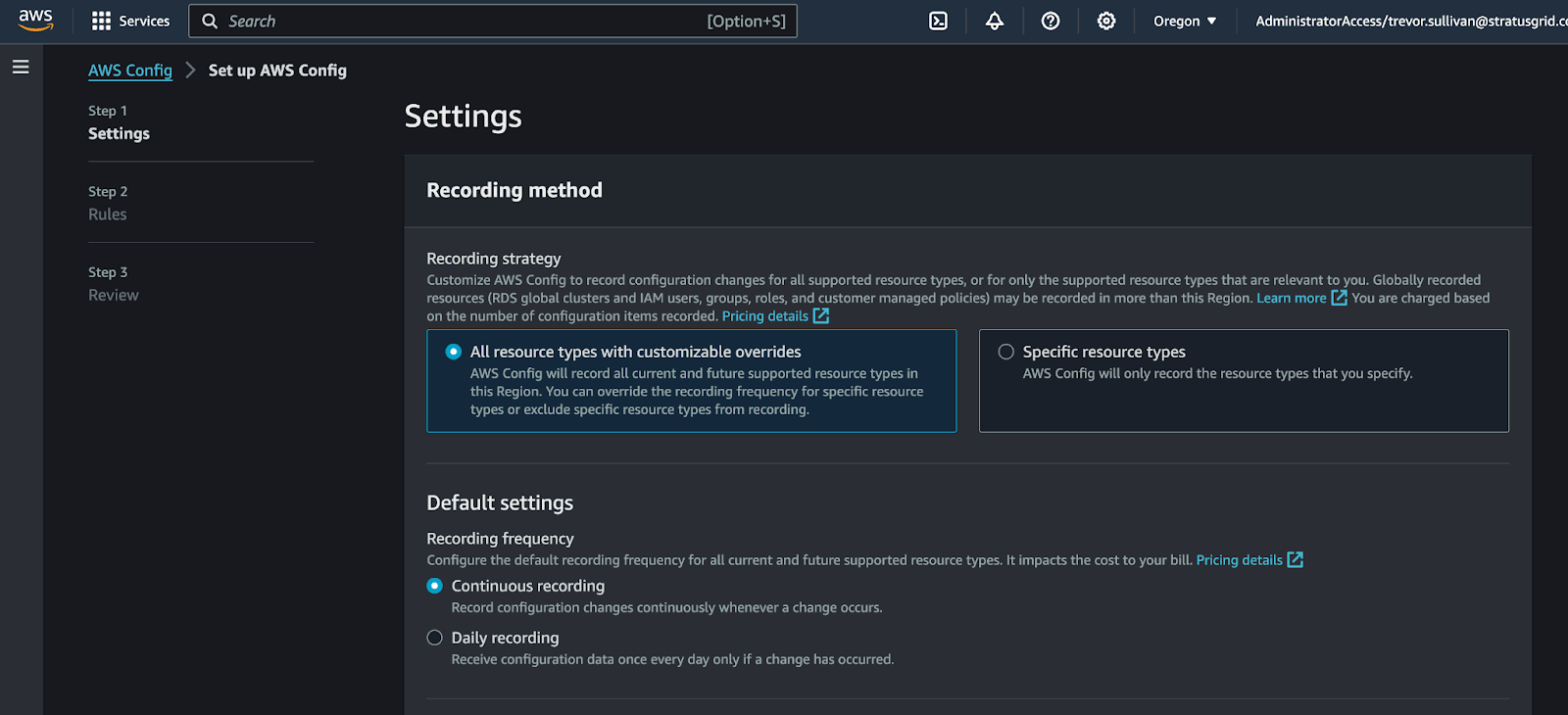
Take note that AWS Config recording is enabled on a per-region, per-account basis by default. You can manage AWS Config recording centrally, across all of your AWS accounts and regions, by utilizing aggregators with AWS Organizations. For this article, we’ll just focus on a single region in a specific AWS account.
Create a Custom Guard Compliance Rule
Once you’ve activated the AWS Config resource configuration recording, you can create a new rule using Guard syntax. The Guard syntax allows you to create “rules” that inspect the resource configuration data gathered by the AWS Config service, and compare it to the desired values. If a resource’s configuration doesn’t match the statements in the rule, then the resource is marked NON-COMPLIANT, otherwise, it’s marked COMPLIANT. You can force a re-evaluation of the rule using the AWS Management Console or the AWS Config APIs via a supported SDK.
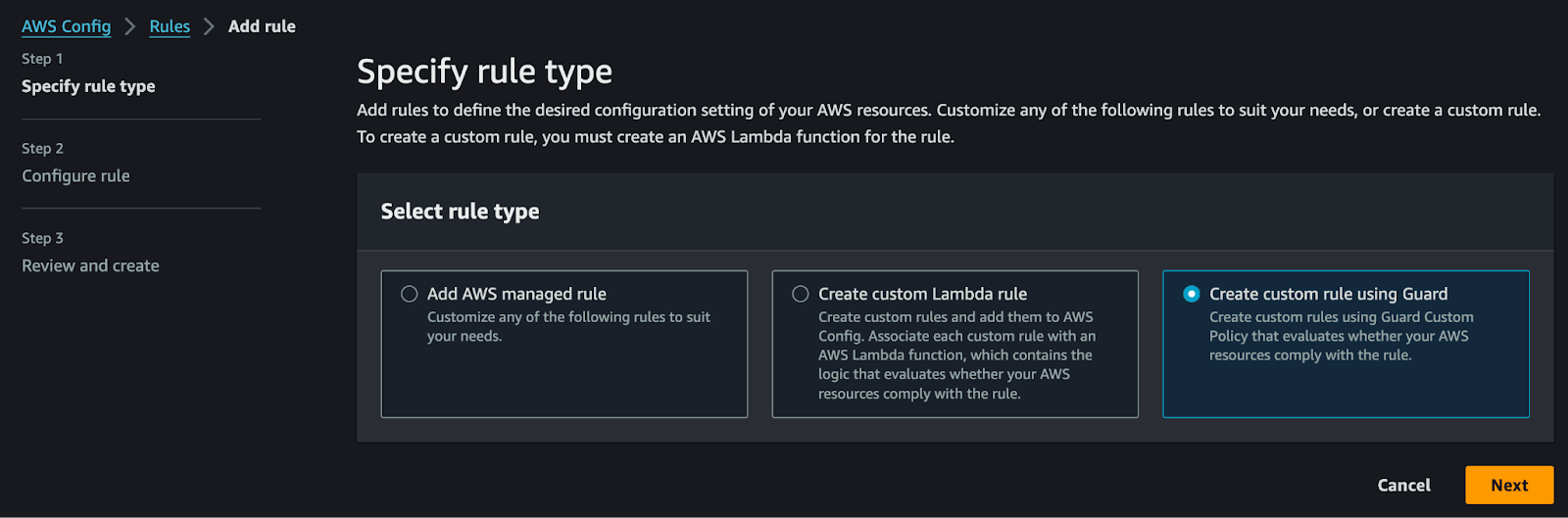
To create the Guard rule, follow these steps:
- Navigate to the AWS Config service
- Click on Rules in the left-hand menu
- Click the Add Rule button
- Select the Create Custom Rule Using Guard option
- Click the Next button
- Provide a rule name, such as rds-ca-certificate-check
- Copy and paste the rule snippet below into the Rule Content text box
- Choose Scope of Changes → Resources
- Select AWS RDS DBInstance from the Resource Type combo box
Steps number 8 and 9 are important because we want to limit this AWS Config rule to apply to specific resource types. It wouldn’t make sense to apply this rule to a different AWS resource type, such as a Lambda function, or an S3 bucket, as those resource types don’t have a CA certificate configuration option.
Use this code snippet for step 7.
rule rds_instances_ca {
configuration.cACertificateIdentifier != "rds-ca-2019"
}
After the AWS Config rule evaluates, you should see a list of your RDS database instances in the Resources In Scope section, along with the compliance status.
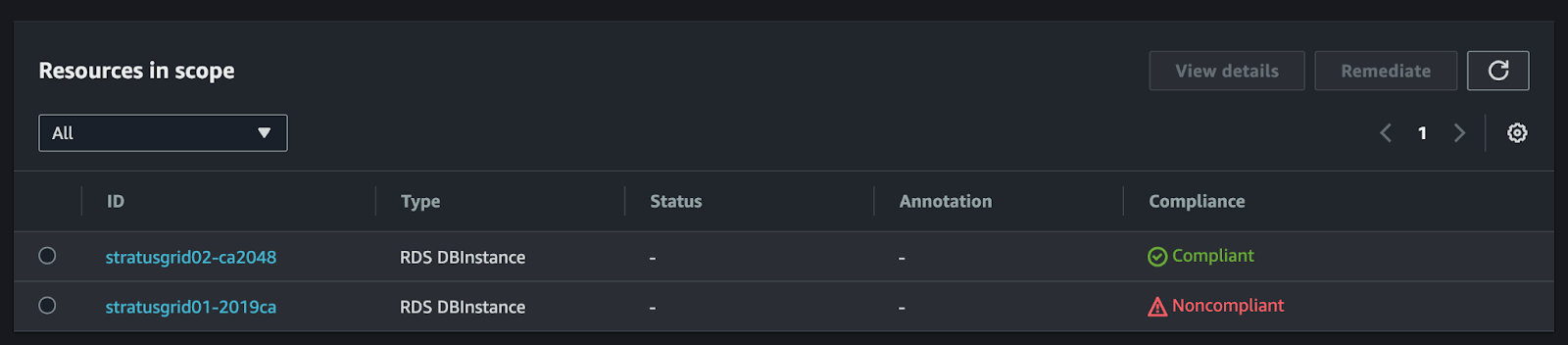
For any non-compliant RDS instances, you can follow the AWS guidance to update the CA certificate.
How to Checking for AWS RDS Instances Using Expiring CA Certificates
The AWS Config service is designed to help validate AWS cloud resource compliance and provides the mechanisms for you to define your own custom policies. Using a simple Guard rule, you can easily detect any non-compliant RDS database instances, using the expiring CA certificate in August 2024. You can use that compliance data to help ensure the continuity of your database services and line of business applications.
For more information, check out these resources.
Need Expert Assistance? Contact StratusGrid Today!
If the sophistication of AWS RDS and CA certificate checks feel too complex, or if you require assistance with any aspect of migration, modernization, stabilization, or optimization of your cloud resources, we're here to help.
Our team of experts is adept at simplifying complex cloud challenges, ensuring your infrastructure is compliant and optimized for performance and cost-efficiency. Contact us now to secure your infrastructure and optimize your cloud investments.
BONUS: Find Out if Your Organization is Ready for The Cloud ⤵️